Using Multiple Identity Providers (IdPs) can assist large enterprise customers in resolving complex authentication and authorization deployments for their Webex Organization. This feature is particularly beneficial for customers undergoing mergers and acquisitions, where multiple IT organizations with different IDPs need to communicate, despite each organization having its own Identity Provider. Government entities and universities often have various organizations, colleges, or agencies that centrally purchase or share the same email domain but operate with separate IT departments. Additionally, multinational organizations may have subsidiaries in different countries with their own distinct IT organizations that require connectivity to the same Webex organization.
Webex has addressed this challenge by introducing a feature that enables customers to configure multiple IDPs with the following capabilities:
- Choose the appropriate Federation Protocol for your organization: Webex supports OpenID Connect (OIDC) or SAML for federation with Webex.
- Webex Identity for users not in your IDP: If a user resides outside your organization’s IDP and you want them to utilize a username and password managed by Webex, you can select Webex Identity as an Identity Provider.
- Routing rules for flexibility and control: Administrators can employ routing rules to direct users to the appropriate identity provider based on Group or Domain.
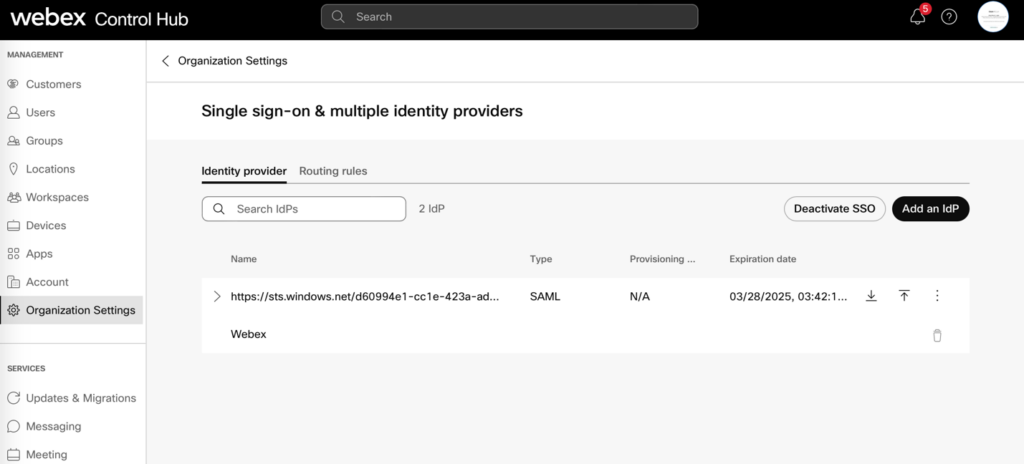
- Security and Auditability: Admins must use a domain verified within their organization for domain-based routing of users. Admin alerts are enabled by default, and configuration changes are automatically logged in the Audit Log.
Other considerations for administrators include the ability to use external users and external admins for Small and Medium-sized Businesses (SMBs) or enterprises that only require authentication of a few users outside their organization. Many enterprises possess robust security IDPs that allow for federation across organizational boundaries. Collaboration admins should closely collaborate with their Identity and Security teams to evaluate the applicability of this feature in addressing their requirements while ensuring compliance with enterprise security and compliance standards.
Deployment Example: Mergers and Acquisitions
Let’s examine a couple of examples demonstrating how to leverage this feature in a practical scenario. Consider a company undergoing a merger and acquisition, where both companies use AzureAD and need to communicate via Webex.
- Identity Proofing: The first step involves verifying the domain of the acquired company within the parent company’s Webex organization using Webex Domain Management. This step is crucial to demonstrate ownership of the domain and activate users during provisioning. By doing so, users can skip the identity verification process during onboarding, and other Webex users can trust the authenticity of these users.
- Identity Provisioning: Next, determine the provisioning method. Since the parent organization uses AzureAD, it is recommended to establish a provisioning agreement using the Microsoft Gallery Application for user provisioning to Webex. In the near future, the AzureAD Wizard will allow the setup of provisioning with multiple AzureAD instances. Initially, assign one admin user to the Gallery Application for testing provisioning and subsequent authentication. Additional users or user groups can be assigned to the Gallery Application once it has passed the User Acceptance Tests.
- Authentication Setup: The parent organization can then configure a SAML or OIDC agreement with the AzureAD Gallery Application. Follow the instructions provided to set up authentication using SAML by exchanging metadata between Webex and the new AzureAD Gallery Application. Ensure the IDP configuration in Webex is tested with the admin user.
- Enable Routing Rule: After successful testing, set up a “routing rule.” In this case, since the users share a consistent domain and the domain has been verified, a domain-based routing rule can be employed. This rule will direct all users provisioned in your organization with the “foo.com” domain to the AzureAD gallery application for authentication.
- Assign Users to the AzureAD Gallery Application for “foo.com”: Once authentication and routing rules have been tested, proceed to assign individual users or user groups to the Gallery Application. These users will be provisioned to Webex, and when they attempt to log in, they will be redirected to the AzureAD instance for “foo.com.”
Other Considerations: Consider utilizing user groups from both AzureAD instances to facilitate licensing and setting templates. This will enhance automation and allow for the assignment of different services to the respective user groups.
For additional information, refer to the following resources: