In today’s digital age, incidents such as cyber-attacks and data breaches have become more prevalent. These incidents can cause significant harm to businesses, including financial losses, damage to company reputation, and loss of customer trust. In fact, the average costs a company incurs from a data breach range from $4 million to $10 million dollars. However, when a breach can be resolved faster, companies can save an average of $1.12M.[1]
When an incident does occur, all communications and collaboration is compromised, including identity systems and network security – putting IT at a disadvantage for quick response. Therefore, it’s essential that companies have a robust incident response plan in place to mitigate the impact of any incidents.
Having a secure, dedicated collaboration solution in place for these scenarios can help companies respond to security incidents faster and more effectively, reducing the risk of damage or loss, and meeting compliance requirements. Webex supports critical capabilities required to manage incident response, including End-to-end encryption, multiple IDP for authentication, native calendars, and group policies in order to provide IT with the most secure, effective way to respond to a security breach.
Groups for Departmental Policies
To further ensure the right controls are in place during a security incident, it’s important to be able to manage users based on specific profile criteria. Webex allows administrators to organize their users based on different organizational profiles for the purposes of creating efficiencies and preventing errors when managing bulk administration. Admins can create policies for license assignment and admin settings at group boundaries so anytime a user joins a group the policy is applied and is removed when a user leaves a group.
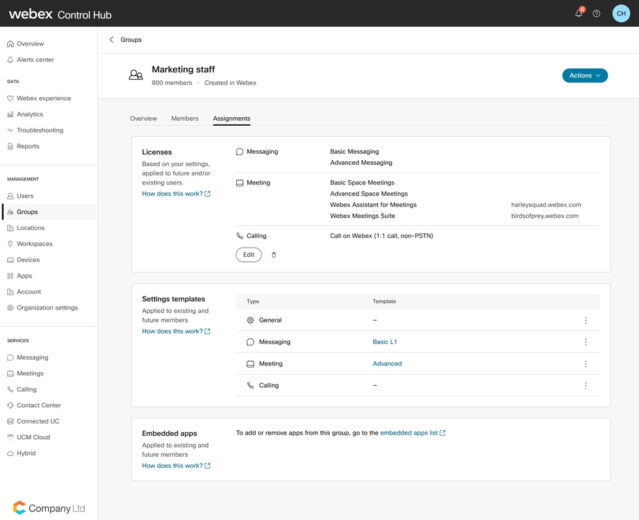
Groups can be easily created in Control Hub by synchronizing them from an on-premises Active Directory through the Cisco Active Directory Connector, IDaaS, or via APIs. For an incident response scenario, native groups in Control Hub can be created without dependence on any IT system and right policies applied so security posture is maintained.
Multiple IDP for User Authentication
Webex Identity plays a critical role in helping organizations respond to ransomware attacks. Admin can proactively plan and have a backup IDP (a cloud IDP or Webex as IDP) setup which is separate from the company’s primary IDP.
In the event of a ransomware attack, where the primary IDP is compromised, admins can quickly sever the SSO configuration from the compromised primary IDP, revoke tokens from all users, and establish SSO with the previously set up backup IDP for selected or all users. This can be achieved with the help of Multiple IDP support within Control Hub, which gives the flexibility to route authentication to different IDPs based on a domain or group.
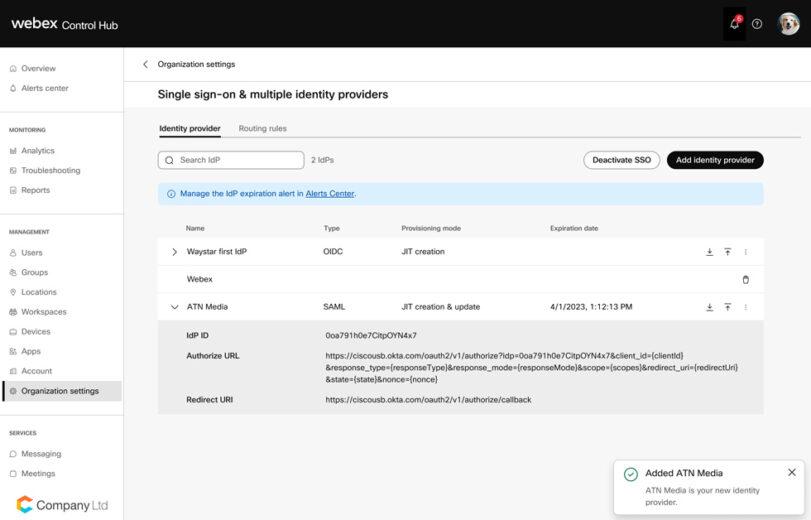
After the authentication with the new IDP has been established, and Admin can use the Webex Security events API to monitor the activity of users using a UBA or SIEM tool and maintain a 360-security view of their users.
Dedicated Native Calendars
Webex enables users to securely manage incident response meetings without the need for a separate calendaring platform. Using the Webex App, users can schedule, host, and access all their meetings in a single place.
End-to-End Encryption and Bring Your Own Key
Webex platform provides a variety of tools to help admins and security teams stay connected and collaborate securely during ransomware attacks. In the unlikely event of a ransomware attack, network security could also be compromised, resulting in Man in the middle attacks (MTM).
In such a scenario, organizations can use Webex End-to-end encrypted (E2EE) meetings. E2EE security protects users’ content from the time it is sent by a user to the time it is received and displayed by other participants in the meeting so that entities in the middle can’t read it or tamper with it. Basically, E2E security prevents the attackers, cloud conferencing provider, and everyone else not in the meeting, from listening to meetings.
Finally, in the meeting participant list, the Webex application indicates whether the participant’s identity has been verified. if Identity is unverified, the host can authenticate unverified participants by asking them to send the security code. Everyone in the meeting should see the same security code, and the code changes each time a new participant joins the meeting to ensure the meeting remains secure. This code provides a very strong defense against impersonation attacks.
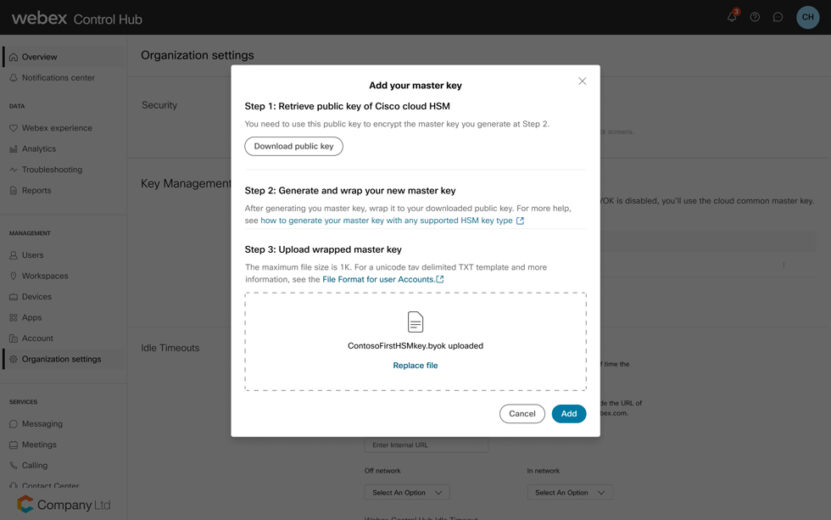
In addition, admins can protect business-critical data by bringing their own encryption key to Webex. This will give them the ability to manage data access in the event of a security compromise. During an attack when an investigation is underway, establishing trust with users and devices, is extremely difficult. Admins can suspend access to data with immediate effect by revoking or in extreme circumstances deleting their main encryption key or frequently rotating key with one click of a button. This helps limit the surface area of the threat and prevent attackers from stealing more information.
After the security breach is contained, admins can either delete the encryption key permanently or rotate it out with a new key to prevent hackers from gaining access to confidential data.
Critical Collaboration Controls
During an attack external communication can be very risky, admins can prevent external users from joining meetings and messaging spaces owned by their organization to minimize this risk.
To provide additional levels of security for confidential conversations, Webex provides extensive meeting controls, including approved external meeting sites, in-meeting management, authenticated sign-in, and BYOD with token-based authentication.
Privacy Controls
To maintain privacy with meetings, host and usage data can be deleted at the user level. This ensures there are no traces of sensitive meetings on this ultra-secure platform.
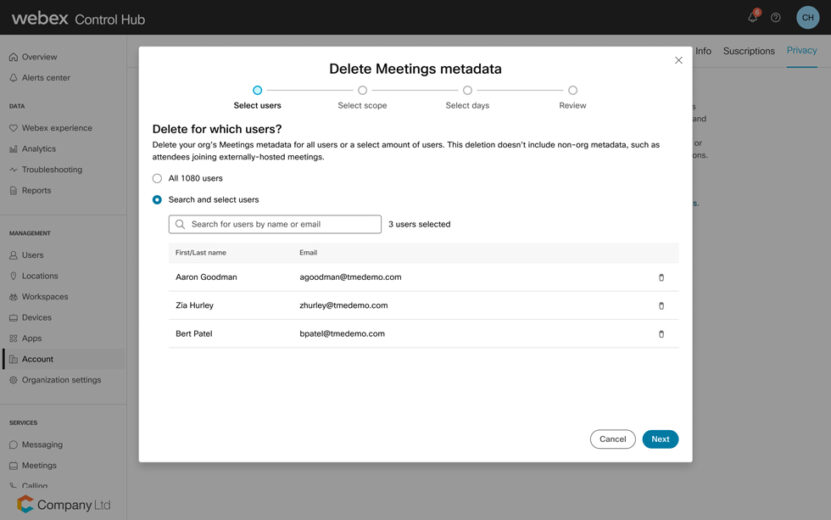
By having a secondary, dedicated collaboration solution, IT admins are able to respond to security incidents faster and more effectively – reducing the risk of damage and sustaining compliance requirements. At Webex, we constantly strive to provide the most secure collaboration portfolio that you can trust. Establishing secure communications during ransomware attacks is critical, and at Webex, we are dedicated to providing the best tools for our customer’s needs.
Learn More:
- Webex Security, Privacy, and Compliance
- Cisco Webex Extended Security Pack just got better with Duo MFA
- Webex audio watermarking – powerful prevention for data leakage
- Webex Data Centers for Improved Privacy and Security
[1]The Cost of a Data Breach, IBM, 2022